
As Digital Identity & Cybersecurity: What You Need to Know in 2025 takes center stage, this opening passage beckons readers into a world crafted with good knowledge, ensuring a reading experience that is both absorbing and distinctly original.
In the evolving landscape of digital identity and cybersecurity, staying informed about the latest trends and advancements is crucial for individuals and organizations alike. This article delves into the key aspects of these topics and what to expect by 2025.
Overview of Digital Identity & Cybersecurity in 2025

In 2025, digital identity and cybersecurity have undergone significant evolution, shaped by technological advancements and increasing cyber threats. It is crucial for individuals and organizations to stay updated with the latest trends to protect sensitive information and maintain secure online presence.
However, with these advancements come potential challenges that need to be addressed to navigate the complex digital landscape effectively.
Evolving Trends in Digital Identity & Cybersecurity
- The adoption of biometric authentication methods such as facial recognition and fingerprint scanning has become more prevalent, enhancing security measures.
- Blockchain technology is increasingly being utilized for secure identity verification and data protection, ensuring transparency and immutability.
- Artificial intelligence and machine learning algorithms are being leveraged to detect and prevent cyber threats in real-time, bolstering cybersecurity defenses.
Importance of Staying Updated
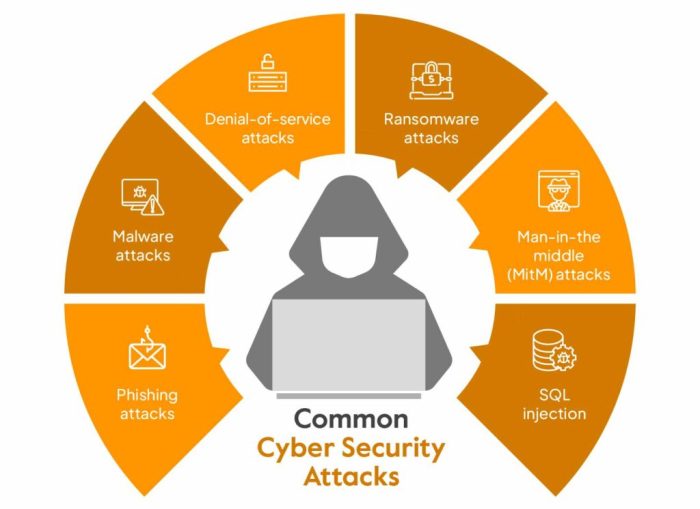
- Regularly updating security software and systems is essential to safeguard against evolving cyber threats like ransomware attacks and data breaches.
- Training employees on cybersecurity best practices and raising awareness about potential risks can help prevent social engineering attacks and insider threats.
- Monitoring regulatory changes and compliance requirements is crucial to ensure data protection and privacy standards are met, avoiding costly penalties.
Potential Challenges in the Digital Landscape
- Cybercriminals are becoming more sophisticated, utilizing advanced tactics like AI-driven attacks and supply chain vulnerabilities to exploit digital identities.
- The proliferation of Internet of Things (IoT) devices increases the attack surface, posing challenges in securing interconnected networks and personal data.
- Balancing convenience with security remains a challenge, as users seek seamless digital experiences while maintaining robust cybersecurity measures.
Role of Biometrics in Digital Identity Verification
Biometric authentication methods are revolutionizing the way we verify digital identities in the modern age. By using unique physical characteristics such as fingerprints, facial features, iris patterns, or voice recognition, biometrics offer a more secure and convenient way to authenticate users compared to traditional password-based systems.
Effectiveness of Biometrics vs. Passwords
Biometric authentication is considered more secure than traditional passwords for several reasons. Firstly, biometric data is unique to each individual and cannot be easily replicated or stolen. This makes it extremely difficult for unauthorized users to gain access to sensitive information.
Additionally, biometric authentication eliminates the need for users to remember complex passwords, reducing the risk of weak passwords or password reuse.
Security and Privacy Implications
While biometrics offer enhanced security, there are also concerns regarding privacy and data protection. Storing biometric data introduces the risk of potential data breaches, leading to the exposure of sensitive personal information. It is crucial for organizations to implement robust security measures to safeguard biometric data and ensure compliance with privacy regulations such as GDPR.
Additionally, there are ethical considerations surrounding the use of biometrics, such as consent and transparency in data collection practices.
Artificial Intelligence in Cybersecurity
Artificial Intelligence (AI) plays a crucial role in enhancing cybersecurity measures by providing advanced capabilities to detect and prevent cyber threats in real-time. AI algorithms can analyze vast amounts of data at high speeds, identify patterns, and anomalies that may indicate potential security breaches, and take proactive measures to mitigate risks.
AI-Powered Threat Detection
- AI can continuously monitor network traffic, user behavior, and system logs to identify suspicious activities that might go unnoticed by traditional security mechanisms.
- Machine learning algorithms can learn from historical data to predict future threats and adapt to evolving cyber threats.
- AI-driven threat intelligence platforms can analyze threat data from multiple sources to provide comprehensive insights into emerging threats.
Real-Time Incident Response
- AI-powered security systems can respond to security incidents in real-time by automatically blocking suspicious traffic, isolating compromised devices, or initiating incident response procedures.
- Automated incident response powered by AI can help reduce response times and minimize the impact of security breaches.
Ethical Considerations
- There are ethical considerations surrounding the use of AI in cybersecurity, including concerns about privacy, bias in AI algorithms, and the potential for AI to be weaponized for cyber attacks.
- Ensuring transparency, accountability, and fairness in AI algorithms is essential to mitigate ethical risks and maintain trust in AI-powered cybersecurity systems.
- Regulatory frameworks and industry standards are needed to govern the ethical use of AI in cybersecurity and protect against potential misuse of AI technologies.
Blockchain Technology and Secure Digital Identities
Blockchain technology is revolutionizing digital identity management by offering a secure and decentralized way to store and verify personal information. Unlike traditional centralized databases, blockchain allows for a distributed ledger system that enhances security and privacy.
Benefits of Using Blockchain for Secure Identity Verification
- Immutable Records: Information stored on the blockchain cannot be altered or tampered with, ensuring the integrity of digital identities.
- Decentralization: Eliminates the need for a central authority, reducing the risk of data breaches and unauthorized access.
- Increased Transparency: Every transaction is recorded on the blockchain, providing a transparent and auditable trail of identity verification activities.
- Enhanced Security: Encryption techniques and consensus mechanisms make blockchain-based identity verification highly secure.
Scalability and Interoperability Challenges of Implementing Blockchain in Digital Identity Systems
- Scalability Issues: Blockchain networks like Bitcoin and Ethereum face challenges in handling a large volume of transactions quickly and efficiently.
- Interoperability Concerns: Different blockchain platforms may not be compatible with each other, hindering seamless integration into existing digital identity systems.
- Regulatory Compliance: Ensuring compliance with data protection regulations and industry standards poses a challenge when implementing blockchain for identity verification.
- User Adoption: Educating users about blockchain technology and its benefits is crucial for widespread adoption of blockchain-based digital identity solutions.
Concluding Remarks
In conclusion, understanding the intricacies of digital identity and cybersecurity is paramount as we approach 2025. Stay vigilant, stay informed, and embrace the future with confidence in safeguarding your digital presence.
Question & Answer Hub
How can I protect my digital identity in 2025?
Ensure to use multi-factor authentication, keep software updated, and be cautious of phishing attempts.
What are the potential risks of biometric data for digital identity verification?
Potential risks include data breaches leading to exposure of sensitive information, as well as concerns about the misuse of biometric data.
How does AI enhance cybersecurity measures?
AI can analyze vast amounts of data to detect patterns indicative of cyber threats, enabling quicker responses and more effective threat prevention.
What are the benefits of using blockchain for secure identity verification?
Blockchain provides immutability, transparency, and decentralization, making it highly secure for identity verification purposes.













