Cybersecurity for Digital Transformation: A Complete Guide
Exploring the realm of Cybersecurity for Digital Transformation: A Complete Guide, readers are invited to embark on a journey that uncovers the intricacies of safeguarding digital initiatives. The following paragraphs offer insights and analyses that shed light on the critical role of cybersecurity in the ever-evolving landscape of digital transformation.
Further details will be provided in subsequent sections, delving into strategies, compliance, challenges, and training programs that form the foundation of a robust cybersecurity framework for digital transformation.
Introduction to Cybersecurity for Digital Transformation
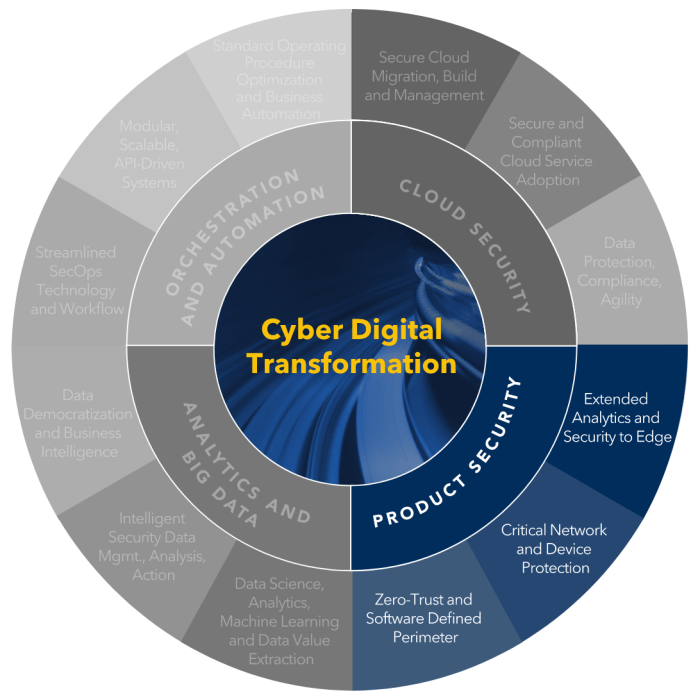
As organizations embrace digital transformation to stay competitive and innovative in today's technology-driven world, the importance of cybersecurity cannot be overstated. Cybersecurity plays a critical role in safeguarding digital assets, data, and systems from cyber threats and attacks.
Defining Cybersecurity in the Context of Digital Transformation
Cybersecurity refers to the practice of protecting digital systems, networks, and data from unauthorized access, cyber threats, and attacks. In the context of digital transformation, cybersecurity becomes essential to ensure the security, privacy, and integrity of digital assets and information.
The Importance of Cybersecurity for Successful Digital Transformation
Cybersecurity is a key enabler of successful digital transformation initiatives. It provides a secure foundation for organizations to leverage emerging technologies, such as cloud computing, Internet of Things (IoT), artificial intelligence, and big data analytics, without compromising data security and privacy.
Challenges and Risks in Cybersecurity for Digital Transformation
However, the digital transformation landscape also presents numerous challenges and risks in terms of cybersecurity. The interconnected nature of digital systems and the proliferation of devices and data create vulnerabilities that can be exploited by cybercriminals. Organizations must navigate issues such as data breaches, ransomware attacks, insider threats, and compliance requirements to ensure robust cybersecurity measures.
Strategies for Implementing Cybersecurity in Digital Transformation
When it comes to implementing cybersecurity in digital transformation, there are several best practices that organizations can follow to ensure the security of their digital assets.
Integrating Cybersecurity Measures
One of the best practices for integrating cybersecurity measures into digital transformation processes is to make security a top priority from the beginning. This involves conducting thorough risk assessments, implementing encryption protocols, and ensuring that security measures are built into every step of the digital transformation journey.
Cybersecurity Frameworks Comparison
There are various cybersecurity frameworks that organizations can choose from to enhance security during digital transformation. Two popular frameworks are NIST Cybersecurity Framework and ISO/IEC 27001. While NIST focuses on identifying, protecting, detecting, responding, and recovering from cybersecurity incidents, ISO/IEC 27001 provides a systematic approach to managing sensitive company information.
Cybersecurity Technologies
Examples of cybersecurity technologies that can enhance digital transformation security include:
- Next-Generation Firewalls: These firewalls offer advanced threat protection capabilities, such as intrusion prevention and detection, application control, and deep packet inspection.
- Endpoint Detection and Response (EDR) Solutions: EDR solutions help organizations detect and respond to advanced threats on endpoints, providing real-time visibility and threat hunting capabilities.
- Security Information and Event Management (SIEM) Systems: SIEM systems collect and analyze security data from various sources to identify and respond to security incidents effectively.
Role of Compliance and Regulations in Cybersecurity for Digital Transformation
Compliance requirements play a crucial role in shaping cybersecurity strategies during the process of digital transformation. Organizations need to adhere to specific regulations and standards to ensure the security of their digital assets and data.
Impact of Compliance Requirements on Cybersecurity Strategies
Compliance requirements have a significant impact on cybersecurity strategies during digital transformation. Organizations are obligated to follow certain guidelines and standards to protect sensitive information and mitigate cybersecurity risks. Failure to comply with these regulations can result in severe consequences, including financial penalties, reputational damage, and loss of customer trust.
- Compliance requirements dictate the implementation of specific security measures to safeguard data privacy and integrity.
- Organizations need to regularly audit and assess their cybersecurity posture to ensure compliance with regulations.
- Non-compliance with regulatory requirements can lead to legal action and fines, impacting the overall financial health of the organization.
Key Regulations and Standards for Cybersecurity in Digital Transformation
There are several key regulations and standards that organizations need to consider when enhancing cybersecurity measures during digital transformation:
- General Data Protection Regulation (GDPR): Ensures the protection of personal data for individuals within the European Union.
- Health Insurance Portability and Accountability Act (HIPAA): Mandates security standards for protecting sensitive patient health information.
- Payment Card Industry Data Security Standard (PCI DSS): Sets requirements for handling credit card information securely.
Implications of Non-Compliance with Cybersecurity Regulations
Non-compliance with cybersecurity regulations during digital transformation can have serious implications for organizations:
Failure to comply with regulations can result in hefty fines, legal actions, and damage to the organization's reputation.
- Non-compliance may lead to data breaches, exposing sensitive information to unauthorized parties.
- Loss of customer trust and loyalty due to perceived negligence in safeguarding data.
- Potential legal consequences and regulatory sanctions for failing to meet cybersecurity requirements.
Addressing Cybersecurity Challenges in Specific Digital Transformation Areas
When it comes to digital transformation, various areas present unique cybersecurity challenges that organizations must address to ensure the security and integrity of their systems and data. Let's delve into some key aspects of cybersecurity in specific digital transformation areas.
Cybersecurity Considerations in Cloud Migration and Adoption
- One of the primary challenges in cloud migration is ensuring the security of data during the transition process.
- Organizations need to implement robust access controls and encryption mechanisms to protect data stored in the cloud.
- Continuous monitoring and auditing of cloud environments are essential to detect and respond to potential security threats.
- Collaboration with cloud service providers to ensure compliance with security standards and regulations is crucial for a secure cloud environment.
Cybersecurity Strategies for IoT Devices and Networks
- Securing IoT devices involves implementing strong authentication mechanisms and encryption protocols to prevent unauthorized access.
- Organizations should regularly update firmware and software on IoT devices to patch vulnerabilities and enhance security.
- Network segmentation and monitoring are essential to isolate IoT devices and detect any unusual behavior that could indicate a security breach.
- Implementing intrusion detection and prevention systems can help organizations identify and respond to cyber threats targeting IoT devices and networks.
Role of Artificial Intelligence and Machine Learning in Enhancing Cybersecurity
- AI and ML technologies can analyze vast amounts of data to identify patterns and anomalies that may indicate potential security threats.
- Machine learning algorithms can enhance threat detection capabilities by learning from past incidents and adapting to new cyber threats.
- Artificial intelligence can automate security processes and responses, enabling organizations to respond to cyber threats in real-time.
- AI-powered security solutions can provide predictive analytics to help organizations proactively address cybersecurity risks before they escalate.
Training and Awareness Programs for Cybersecurity in Digital Transformation
In the realm of digital transformation, it is crucial to design and implement effective training and awareness programs for cybersecurity. These programs play a vital role in educating employees on best practices for ensuring the security of digital assets and data.
By fostering a cybersecurity-aware culture within organizations, the risks associated with digital transformation can be significantly mitigated.
Importance of Creating a Cybersecurity-Aware Culture
- Developing a cybersecurity-aware culture helps instill a sense of responsibility among employees towards safeguarding sensitive information.
- Employees become more vigilant and proactive in identifying and reporting potential cyber threats, thus enhancing the overall security posture of the organization.
- By promoting a culture of cybersecurity awareness, organizations can reduce the likelihood of successful cyber attacks and data breaches.
Measuring the Effectiveness of Cybersecurity Training
- Regular assessments and quizzes can be conducted to gauge employees' understanding of cybersecurity concepts and best practices.
- Monitoring the frequency of reported security incidents can serve as an indicator of the effectiveness of training programs.
- Feedback from employees on the relevance and usefulness of the training can help in refining and improving future training initiatives.
Last Word
In conclusion, the discussion encapsulates the essence of Cybersecurity for Digital Transformation: A Complete Guide, emphasizing the necessity of proactive cybersecurity measures in fostering secure and successful digital metamorphoses. As organizations navigate the complex terrain of digital transformation, a comprehensive understanding of cybersecurity becomes paramount for safeguarding against threats and ensuring a seamless transition into the digital age.
Helpful Answers
What are the key elements of a cybersecurity framework for digital transformation?
The key elements include risk assessment, threat detection, incident response planning, and continuous monitoring to ensure a proactive security posture.
How can organizations measure the effectiveness of cybersecurity training programs?
Effectiveness can be measured through simulated phishing exercises, knowledge assessments, and tracking improvements in security awareness and incident response.
What role does artificial intelligence play in enhancing cybersecurity for digital transformation?
AI is instrumental in automating threat detection, identifying anomalies in network behavior, and improving incident response capabilities for enhanced cybersecurity in digital transformation.