How to Implement Secure Digital Identity Verification: A Comprehensive Guide
Delving into the realm of secure digital identity verification opens up a world of possibilities and challenges. This guide aims to shed light on the intricacies of implementing a foolproof system, ensuring data protection and user security in the digital landscape.
Exploring the nuances of digital identity verification unveils a landscape where technology and security converge to create a robust framework for safeguarding sensitive information.
Understanding Digital Identity Verification

Digital identity verification refers to the process of confirming the identity of an individual using digital methods and technology. It is crucial in today's digital age to ensure secure transactions, prevent fraud, and protect sensitive information.Traditional identification methods, such as presenting physical IDs or answering security questions, pose various challenges.
These methods are susceptible to theft, loss, or impersonation, leading to identity theft and fraud. Moreover, they can be time-consuming and inconvenient for both businesses and customers.Implementing secure digital identity verification offers numerous benefits. It enhances security by utilizing advanced technologies like biometrics, two-factor authentication, and encryption to verify identities accurately.
This reduces the risk of fraud and unauthorized access to personal information. Additionally, digital verification processes are often more efficient, cost-effective, and user-friendly compared to traditional methods.
The Importance of Secure Digital Identity Verification
- Enhances security through advanced technologies like biometrics and encryption.
- Reduces the risk of fraud and unauthorized access to sensitive information.
- Improves efficiency, cost-effectiveness, and user experience compared to traditional methods.
Technologies for Secure Digital Identity Verification
Biometric authentication technologies play a crucial role in ensuring secure digital identity verification. By using unique physical characteristics such as fingerprints, facial features, or iris patterns, biometric authentication provides a highly secure method of confirming an individual's identity.
Comparing Two-Factor Authentication with Multi-Factor Authentication
Two-factor authentication (2FA) requires users to provide two different types of credentials to verify their identity, such as a password and a unique code sent to their phone. On the other hand, multi-factor authentication (MFA) goes a step further by requiring additional verification methods beyond the two factors, such as biometric data or security questions.
While 2FA provides an extra layer of security compared to just a password, MFA offers even greater protection against unauthorized access.
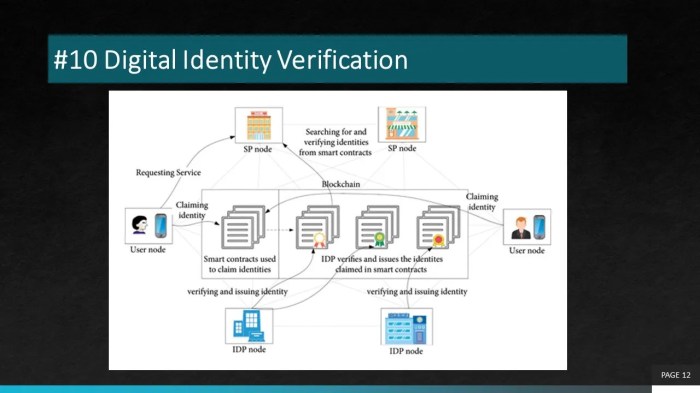
Exploring the Role of Blockchain in Digital Identity Verification
Blockchain technology has the potential to revolutionize digital identity verification by securely storing and managing identity information in a decentralized, tamper-proof manner. By leveraging blockchain's immutable ledger system, individuals can have greater control over their personal data and reduce the risk of identity theft.
Additionally, blockchain can enable secure authentication processes without the need for intermediaries, making digital identity verification more efficient and transparent.
Implementing Secure Digital Identity Verification
Implementing a secure digital identity verification system is crucial to ensure the protection of sensitive data and prevent identity theft. By following specific steps and utilizing advanced technologies, organizations can establish a robust system that safeguards user identities effectively.
Setting Up a Secure Digital Identity Verification System
- Choose a reliable identity verification provider that offers features such as biometric authentication, document verification, and liveness detection.
- Integrate the verification system with your existing platforms or applications to streamline the verification process for users.
- Implement multi-factor authentication to add an extra layer of security and ensure that only authorized individuals can access sensitive information.
- Regularly update and monitor the system to identify and address any vulnerabilities or potential security threats.
The Importance of Data Encryption in Identity Verification Processes
Data encryption plays a critical role in protecting sensitive information during the identity verification process. By encrypting data in transit and at rest, organizations can ensure that personal data is secure and cannot be intercepted or accessed by unauthorized parties.
Encryption helps maintain the confidentiality and integrity of user data, enhancing overall security and compliance with data protection regulations.
The Role of Machine Learning in Enhancing the Security of Digital Identity Verification
- Machine learning algorithms can analyze vast amounts of data to detect patterns and anomalies that may indicate fraudulent activity during the verification process.
- By continuously learning from new data and adapting to evolving threats, machine learning models can improve the accuracy and efficiency of identity verification systems.
- Machine learning can also help automate decision-making processes, reducing the risk of human error and ensuring consistent and reliable verification results.
Compliance and Regulations

In the digital age, compliance with regulations is crucial for organizations implementing digital identity verification solutions. Failure to adhere to key data protection laws can result in severe consequences, including hefty fines and damage to reputation.
Key Regulations Impacting Digital Identity Verification
- The General Data Protection Regulation (GDPR): GDPR sets strict guidelines for the collection, processing, and storage of personal data of individuals within the European Union. Organizations must ensure that they have explicit consent before collecting and processing any personal information for identity verification purposes.
- The Payment Services Directive 2 (PSD2): PSD2 aims to enhance the security of online payments and protect consumers' financial information. It requires strong customer authentication (SCA) for electronic transactions, which may involve using two or more factors to verify the customer's identity.
Importance of Compliance in Identity Verification
- Protecting Personal Data: Compliance with data protection laws ensures that individuals' personal information is safeguarded and used responsibly.
- Building Trust: Demonstrating compliance with regulations enhances trust with customers, showing that their data is handled securely.
- Avoiding Legal Consequences: Non-compliance can lead to legal penalties, fines, and reputational damage for organizations.
Ensuring Compliance in Digital Identity Verification
- Implementing Privacy by Design: Organizations should embed privacy and data protection measures into the design of their identity verification solutions from the outset.
- Conducting Regular Audits: Regular audits and assessments help organizations identify and address any compliance gaps in their identity verification processes.
- Employee Training: Providing comprehensive training to employees on data protection laws and regulations ensures that they understand their responsibilities in handling sensitive information.
- Partnering with Compliance Experts: Collaborating with legal and compliance experts can help organizations navigate complex regulatory requirements and ensure compliance in their identity verification practices.
Last Word
In conclusion, mastering the art of secure digital identity verification is not just a necessity but a strategic advantage in today's data-driven world. By implementing the right technologies and compliance measures, organizations can fortify their systems and build trust with users.
Questions and Answers
How can biometric authentication enhance digital identity verification?
Biometric authentication adds an extra layer of security by using unique biological traits like fingerprints or facial recognition to verify identities.
What is the role of blockchain in digital identity verification?
Blockchain technology provides a decentralized and secure way to store and verify digital identities, reducing the risk of data breaches.
How does data encryption contribute to secure digital identity verification?
Data encryption ensures that sensitive information is protected from unauthorized access, enhancing the overall security of identity verification processes.
Why is compliance with regulations like GDPR crucial for digital identity verification?
Compliance with regulations like GDPR ensures that user data is handled ethically and transparently, maintaining trust and security in identity verification procedures.